Migration to Lightning
Tips for Rolling out Lightning
Main Obstacles
- JavaScript Buttons and Links
- Use of 3rd Party JavaScript libs
JavaScript Buttons and Links
JavaScript buttons and links are types of actions in the Salesforce Classic UI that allow you to create inline JavaScript code that can be invoked via a button or link embedded on a record or list page.
Issue - security challenges
Combining untrusted JavaScript from multiple sources and authors together with the application source code, while maintaining trust of the overall application, has significant security challenges.
On-Click JavaScript buttons have risks that made Salesforce to look for alternatives that you can use for customizing the application.
Without some safeguards, the components would have access to each other’s data, shared access to the window and event structures, and access to any client side API.
Salesforce Locker Service prevents:
- XSS (Cross-site Scripting) and similar security issues
- Unrestricted DOM access
- Calling undocumented/private APIs
Solution
The new approach to JavaScript button functionality in Lightning Experience that is better for everyone.
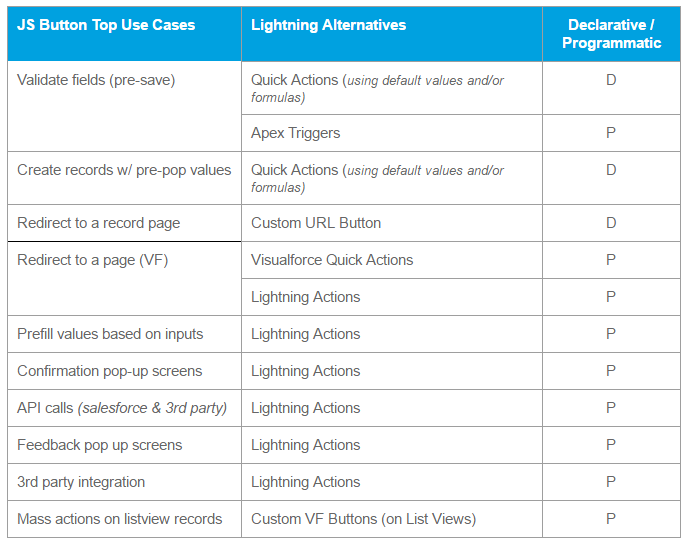
Typical use cases for using JavaScript buttons in Classic
- Use or manipulate values on a record before the save
- Validate fields — ensure values are populated and/or meet criteria
- Prefill values based on inputs in other fields
- Redirect to a Visualforce page based on input values
- Confirmation pop-up screens
- Create records w/ pre-populated values
- Trigger flows from Visual Workflow
- Callouts to Salesforce or external API
- 3rd party integration
- Mass actions on records in a list
- Feedback pop-up screens for users, directing methods and procedures
Use cases for JavaScript buttons and alternate better–solutions in Lightning
Quick Actions Demos
Use Case: Validate Fields when the user closes the Task
Redirect to a Visualforce Pags with Account Record Field Values :
Use case:
JavaScript buttons are commonly used to read and pass values from a record into a URL that redirects users to a Visualforce page.
An alternative way to have your users access Visualforce pages is via quick actions
Demo
Custom Link demo
Types of Actions
- Global Actions
- Object Specific Actions
Global Actions
Global actions let users create records, but the new record has no relationship with other records.
Global actions can’t update a record.
Global Actions can be put anywhere actions are supported:
- on record detail pages
- the feed or Chatter groups
Global Publisher Layouts
The global layout only applies to the action bar in places like:
- Feed
- Chatter groups
only on pages that aren’t related to a specific object since it is GLOBAL!
After creating global publisher layouts, you can assign them to different user profiles.
Global Action Demo
Object-specific Actions
Object-specific actions let users create or update records in the context of a particular object.
Example: An action associated with the Opportunity object is only available when a user is looking at an Opportunity.
Object-specific Actions can:
create records that are automatically associated with related information.
Examples:
- simultaneously create a Contact and associates it with an Account
- create an action (Event) that will appear on the Contact detail page
update records
- make object-specific actions available to the users by editing object's page layout.
Object-Specific Action Demo
About XSS
Cross-site Scripting (XSS) refers to client-side code injection attack wherein an attacker can execute malicious scripts (also commonly referred to as a malicious payload) into a legitimate website or web application. XSS is amongst the most rampant of web application vulnerabilities and occurs when a web application makes use of unvalidated or unencoded user input within the output it generates.
By leveraging XSS, an attacker does not target a victim directly. Instead, an attacker would exploit a vulnerability within a website or web application that the victim would visit, essentially using the vulnerable website as a vehicle to deliver a malicious script to the victim’s browser.
While XSS can be taken advantage of within VBScript, ActiveX and Flash (although now considered legacy or even obsolete), unquestionably, the most widely abused is JavaScript – primarily because JavaScript is fundamental to most browsing experiences.