Deterministic Encryption
What is Deterministic Encryption ?
Produces the same ciphertext for a given plaintext and key, even over separate executions of the encryption algorithm. While Probabilistic encryption uses randomness in an encryption algorithm, so that when encrypting the same message several times it will, in general, yield different ciphertexts.
Examples of Deterministic Encryption:
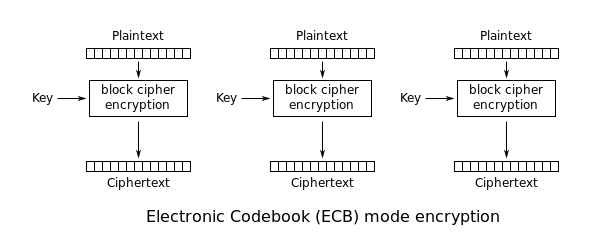
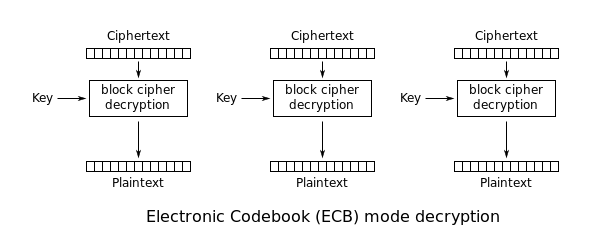
RSA cryptosystem (without encryption padding), and many block ciphers when used in ECB (Electronic Codebook: the message is divided into blocks, and each block is encrypted separately.) mode or with a constant initialization vector.
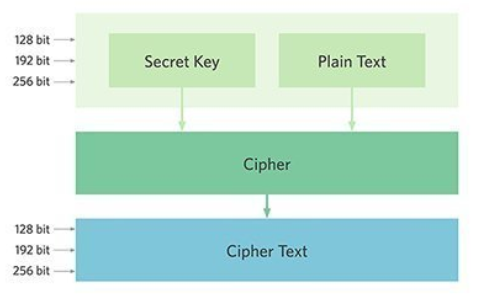
What is AES (Advanced Encryption Standard)?
Symmetric block cipher chosen by the U.S. government to protect classified information and is implemented in software and hardware throughout the world to encrypt sensitive data.
Comprises three block ciphers: AES-128, AES-192 and AES-256
Each cipher encrypts and decrypts data in blocks of 128 bits using cryptographic keys of 128-bits, 192-bits and 256-bits, respectively
What is DES (Data Encryption Standard)?
- A symmetric-key algorithm for the encryption of electronic data. Although insecure, it was highly influential in the advancement of modern cryptography.
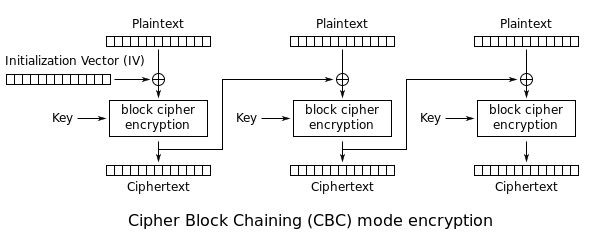
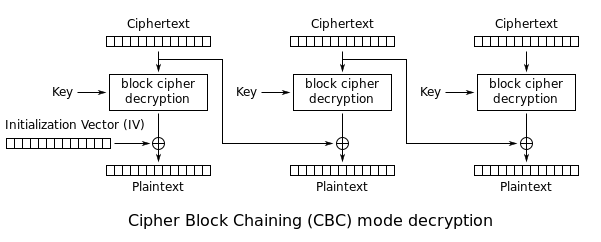
What is CBC (Cipher Block Chaining)?
- Each block of plaintext is XORed with the previous ciphertext block before being encrypted.
- This way, each ciphertext block depends on all plaintext blocks processed up to that point.
- To make each message unique, an initialization vector (IV: is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom. ) must be used in the first block.
What is ECB (Electronic Codebook)?
- The message is divided into blocks, and each block is encrypted separately.
Salesforce Shield Support for Deterministic Encryption
- The users can filter records in reports and list views, even when the underlying fields (data-at-rest) are encrypted.
- Supports WHERE clauses in SOQL queries and is compatible with unique and external ID fields
- Supports single-column indexes and single-column case-sensitive unique indexes
Uses the Advanced Encryption Standard (AES) with 256-bit keys with CBC mode, and a static initialization vector (IV).
One primary motivation for the use of deterministic encryption is the efficient searching of encrypted data. If the database entries were encrypted with a deterministic scheme and sorted, then a specific field of the database could be retrieved in logarithmic time.
By default, Salesforce encrypts data using a probabilistic encryption scheme. Each bit of data is turned into a fully random ciphertext string every time it’s encrypted. Encryption doesn’t generally impact users who are authorized to view the data. The exceptions are when logic is executed in the database or when encrypted values are compared to a string or to each other. In these cases, because the data has been turned into random, patternless strings, filtering isn’t possible.
-- if the LastName field is encrypted with probabilistic encryption,
-- you can’t run this query. Deterministic encryption addresses this problem.
SELECT firstName FROM Contact WHERE LastName = 'Smith'
To be able to use filters when data is encrypted, we have to allow some patterns in our data.
Deterministic encryption uses a static initialization vector (IV) so that encrypted data can be matched to a particular field value. The system can’t read a piece of data that’s encrypted, but it does know how to retrieve the ciphertext that stands for that piece of data with the help of this static IV.
The IV is unique for a given field in a given org and can only be decrypted with your org-specific encryption key.
We evaluate the relative strengths and weaknesses of cryptographic approaches based on the types of attacks that can be launched against a particular algorithm.
We also consider the length of time that it could take for the attack to succeed. For example, it is commonly said that a brute-force attack against an AES 256-bit key would take a billion billion years given current computing capabilities. Nevertheless, it is common practice to rotate keys regularly.
Certain kinds of attacks become a bit less far-fetched when you get away from purely random ciphertext.
For example, an attacker could conceivably analyze deterministically encrypted ciphertext and determine that the cleartext string Alice always resolves to the ciphertext YjNkY2JlNjU5M2JkNjk4MGJiNWE2NGQ5NzI5MzU1OTcNCg==. Given enough time to eavesdrop, an attacker could defeat encryption by building a dictionary of cleartext values to ciphertext values.
Just enough determinism: decrease encryption strength as minimally necessary to allow filtering
The Salesforce Shield approach is to expose just enough determinism to enable bona fide users to filter on encrypted data while limiting it enough to ensure that a given plaintext value does not universally result in the same ciphertext value across all fields, objects, or orgs. Even if an attacker successfully matched cleartext to encrypted values for one field, the attacker would have to do it all over again for any other field, and again for the same field in another object.
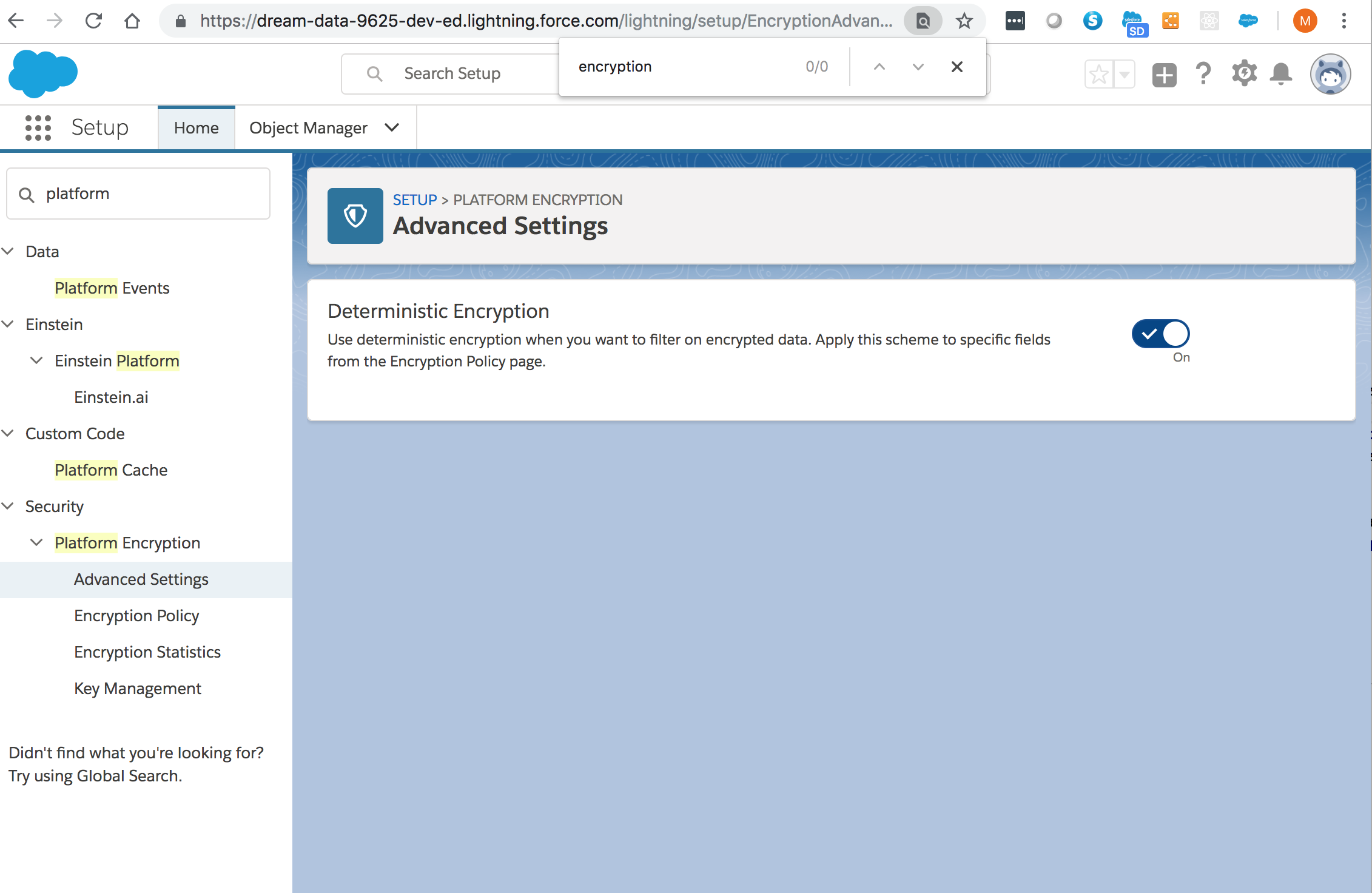
How to setup Salesforce Deterministic Encryption
From Setup > Platform Encryption > Advanced Settings: Enable Deterministic Encryption:
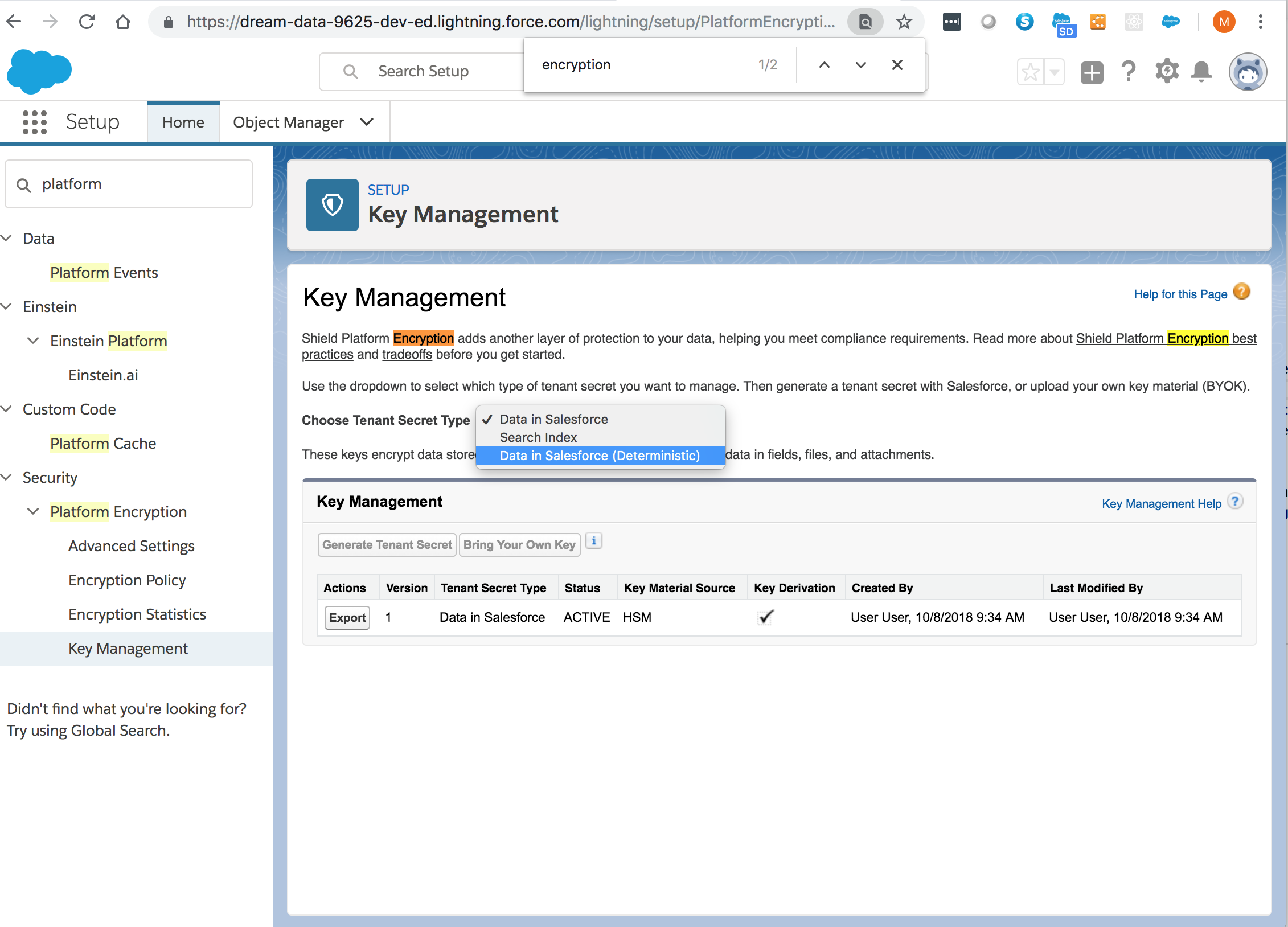
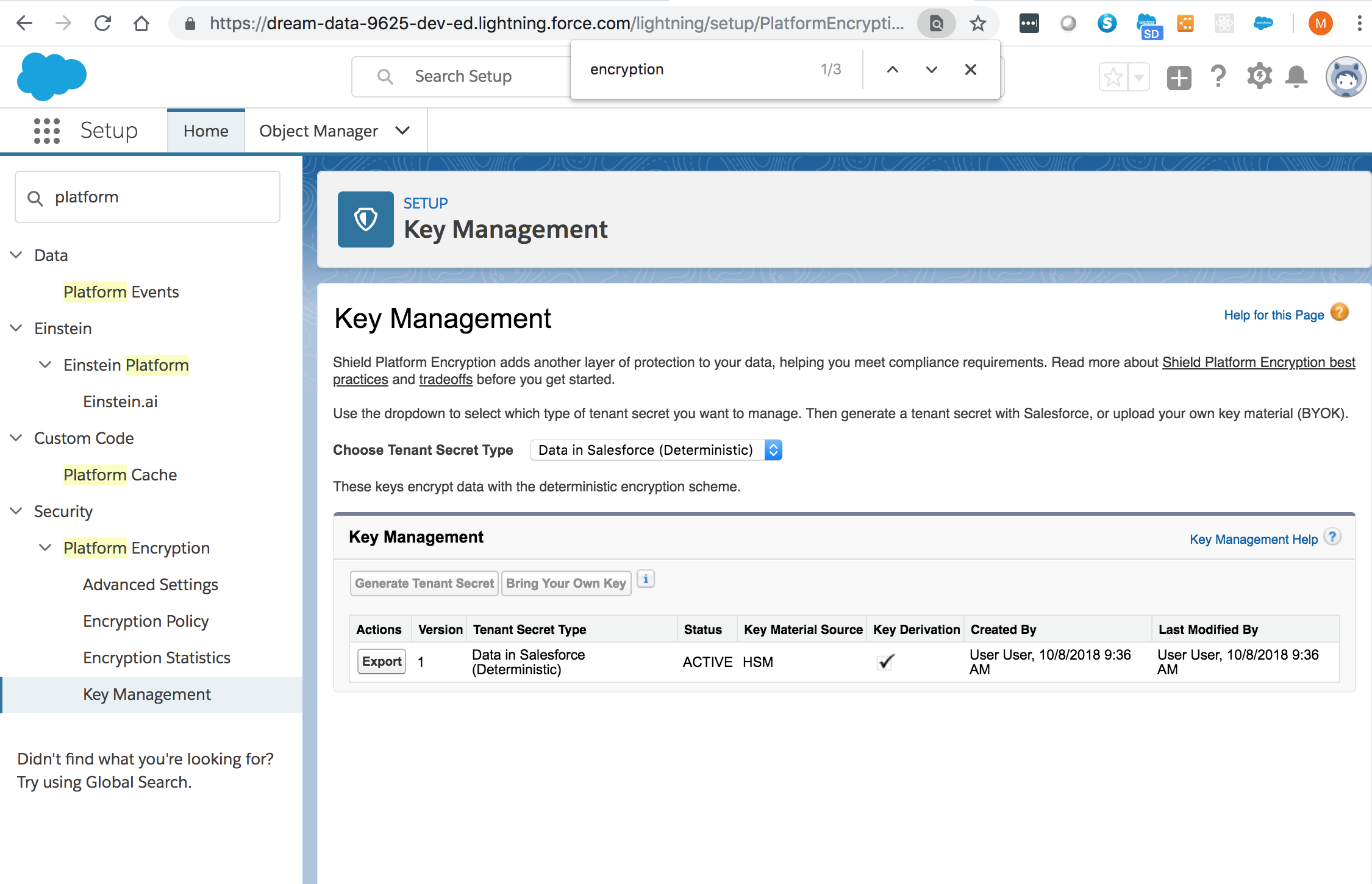
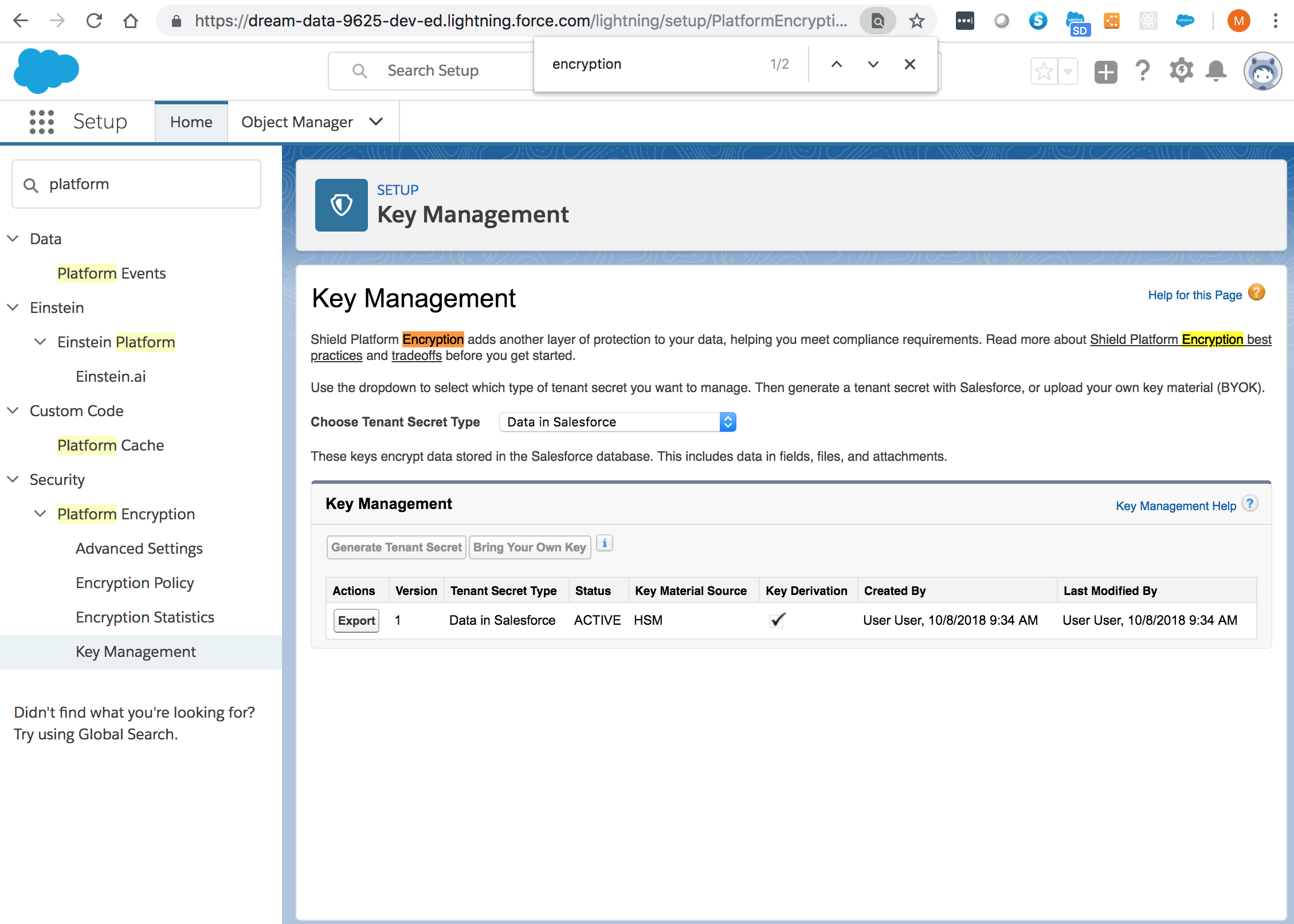
From Setup > Key Management: Select the Data in Salesforce (Deterministic) secret type:
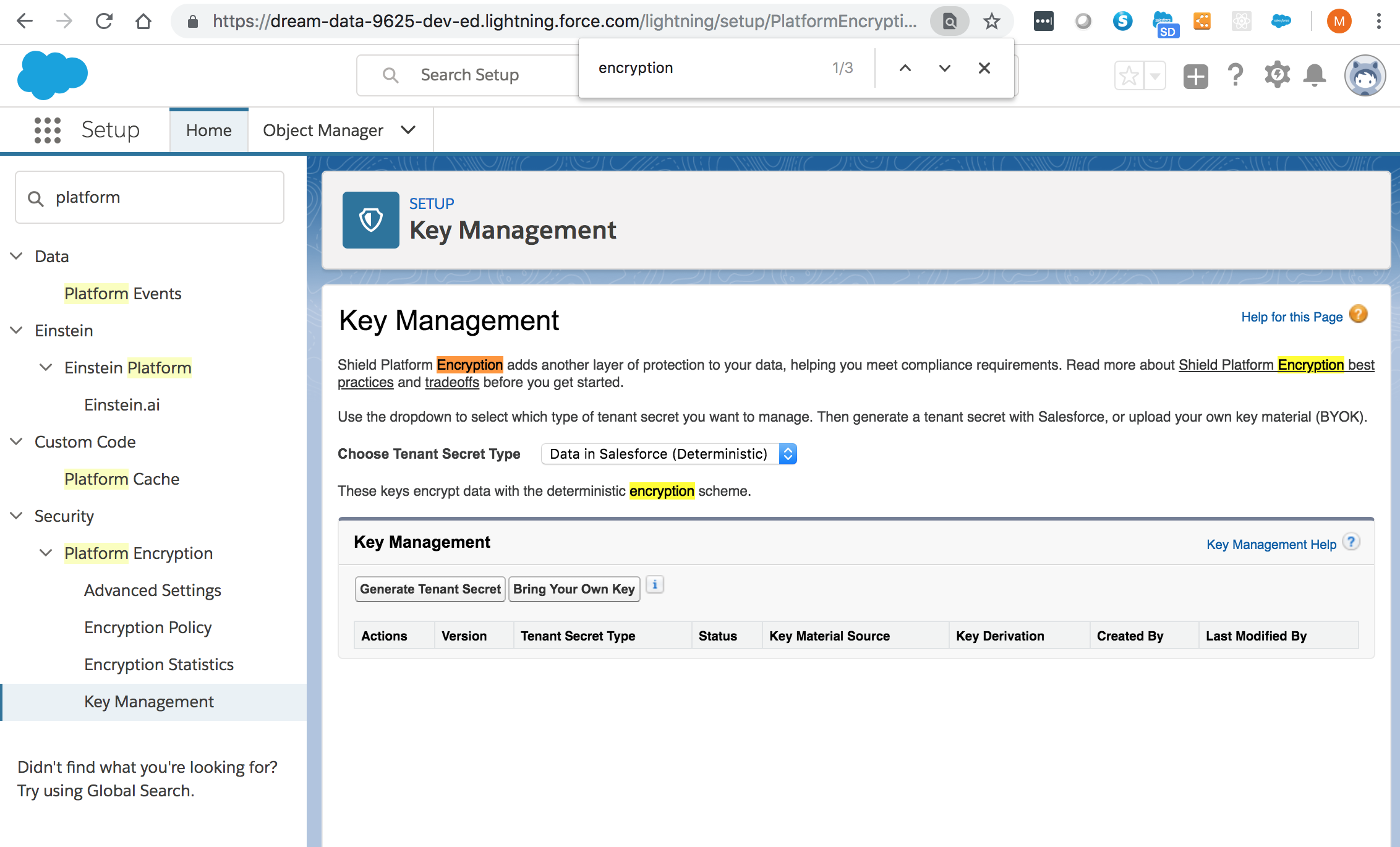
 Generate a tenant secret:
You can mix and match probabilistic and deterministic encryption, encrypting some fields one way and some fields the other.
Generate a tenant secret:
You can mix and match probabilistic and deterministic encryption, encrypting some fields one way and some fields the other.
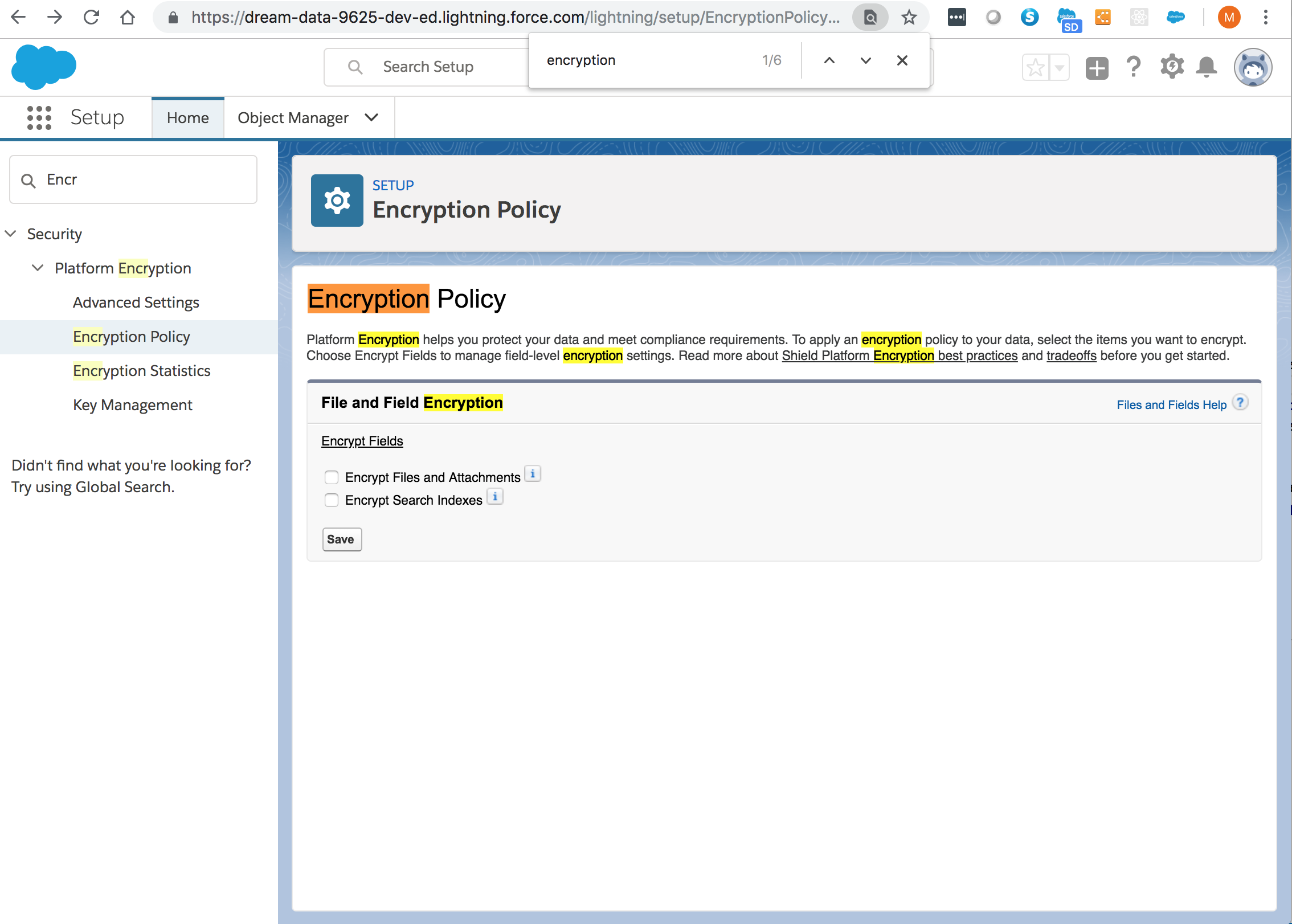
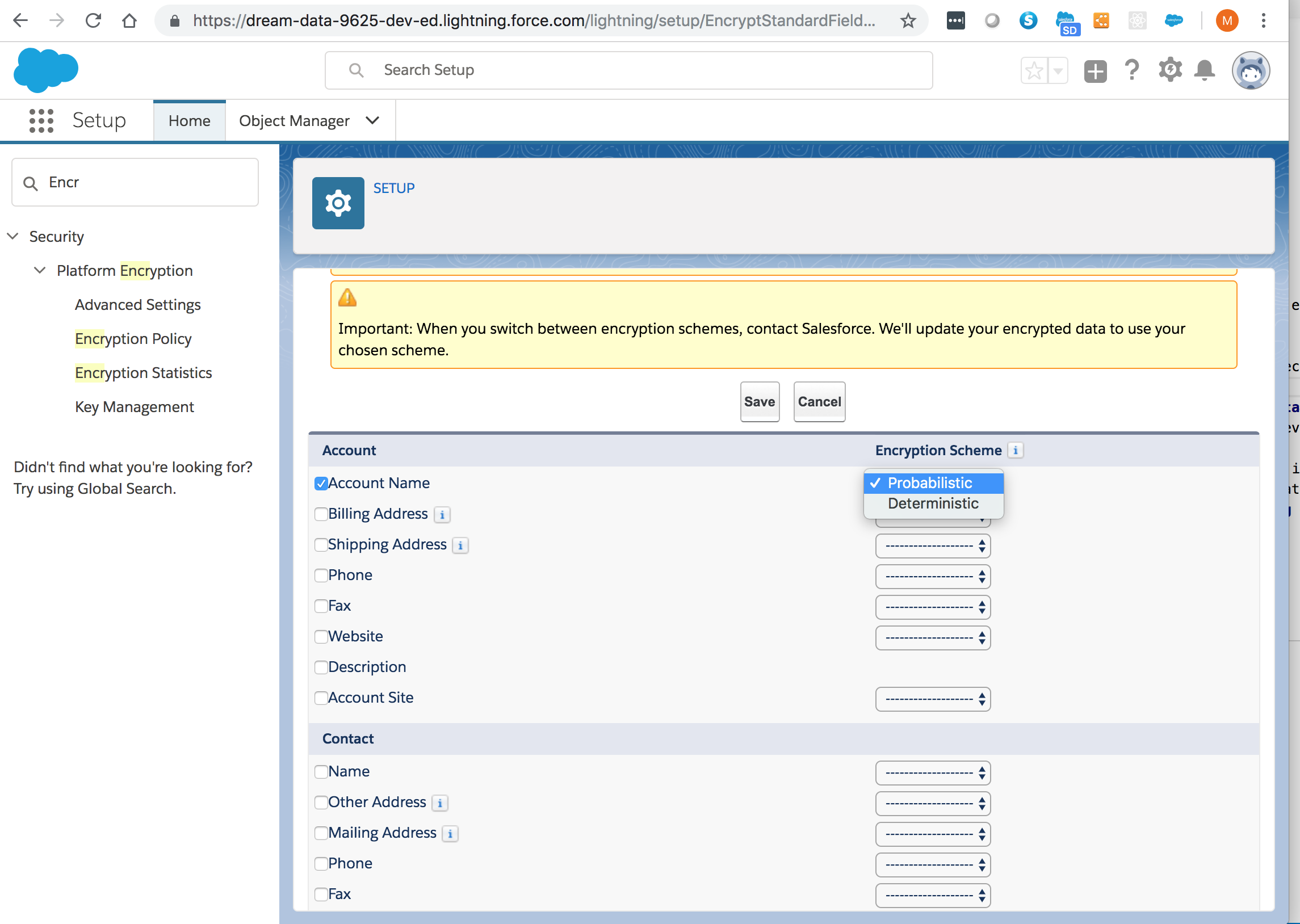
 Enable encryption for each field, specifying the deterministic encryption scheme. How you do that depends on whether it’s a standard field or a custom field.
Enable encryption for each field, specifying the deterministic encryption scheme. How you do that depends on whether it’s a standard field or a custom field.
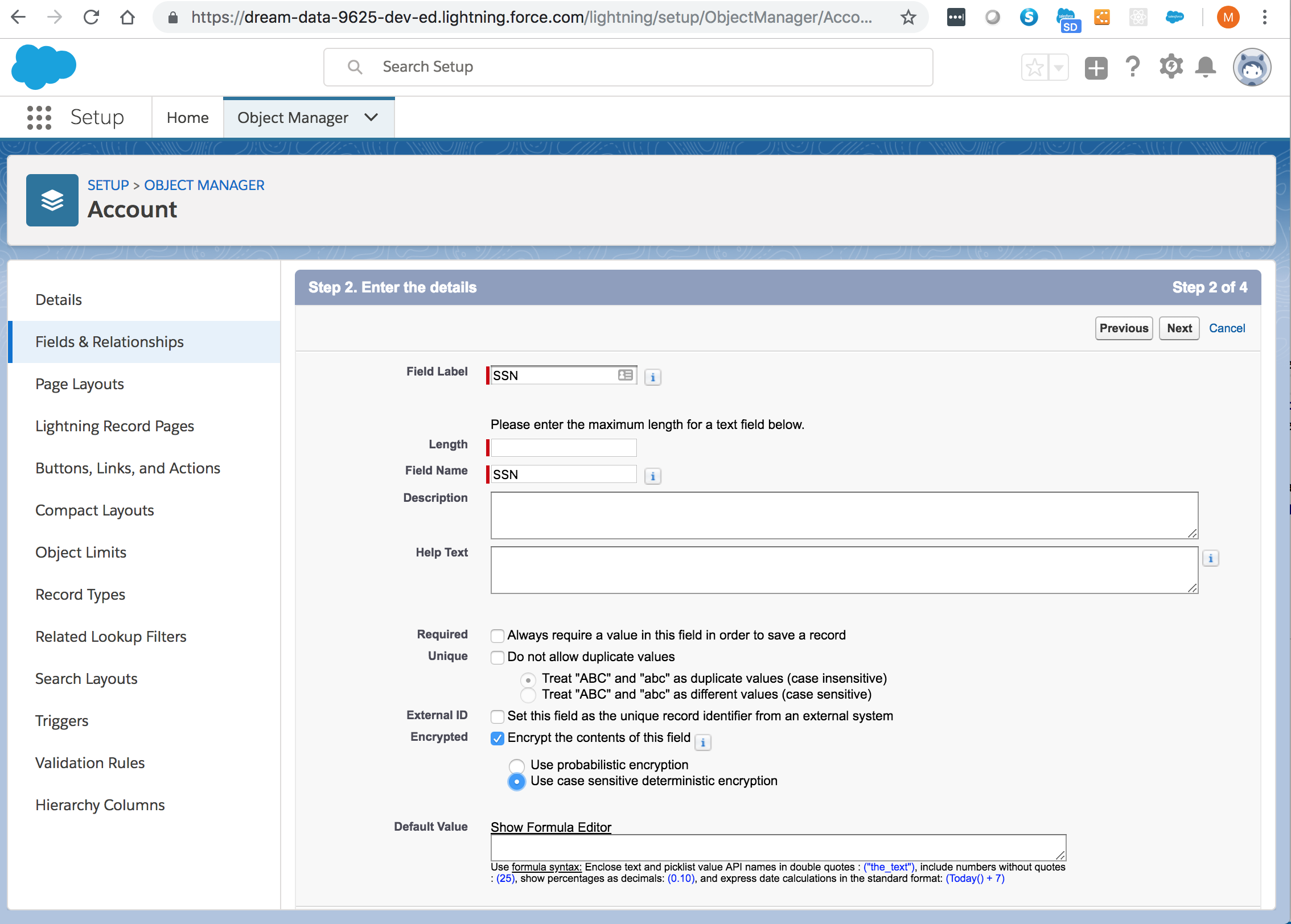
 For custom fields, open the Object Manager and edit the field you want to encrypt. Select Encrypt the contents of this field, and select Use case sensitive deterministic encryption.
For custom fields, open the Object Manager and edit the field you want to encrypt. Select Encrypt the contents of this field, and select Use case sensitive deterministic encryption.
Considerations for Using Deterministic Encryption
Refer: Considerations for Using Deterministic Encryption
Key Rotation and Filter Availability
To filter and execute queries on fields with unique attributes, new and existing encrypted data must be encrypted with the active Data in Salesforce (Deterministic) key material.
Available Fields and Other Data
The deterministic encryption option is available for custom URL, email, phone, text, and text area field types. It isn’t available for the following types of data:
- Custom date, date/time, long text area, or description field types
- Chatter
- Files and attachments
Filter Operators
In reports and list views, the operators equals and not equal to are supported with deterministic encryption. Other operators, like contains or starts with don’t return an exact match and aren’t supported.
Case Sensitivity
When you use deterministic encryption, case matters.
In reports, list views, and SOQL queries on encrypted fields, the results are case-sensitive. Therefore, a SOQL query against the Contact object, where LastName = 'Jones’, returns only Jones, not jones nor JONES. Similarly, when the filter-preserving scheme tests for unicity (uniqueness), each version of “Jones” is unique.
API Options to Identify Filterable Fields
Fields encrypted using the deterministic encryption scheme are filterable. You can use the isFilterable() method to determine the encryption scheme of a particular encrypted field. If the field is filterable, the method returns true.
However, you can’t explicitly detect or set the deterministic encryption scheme via the API.
External ID
You can enable the external ID for deterministically encrypted fields when you use the Unique - Case-Sensitive attribute. External ID isn’t available for email field types
However, you can’t explicitly detect or set the deterministic encryption scheme via the API.
Compound Names
Even with deterministic encryption, some kinds of searches don’t work when data is encrypted. Concatenated values, such as compound names, aren’t the same as the separate values. For example, the ciphertext for the compound name William Jones is not the same as the concatenation of the ciphertexts for William and Jones.
So, if the First Name and Last Name fields are encrypted in the Contacts object, this query doesn’t work:
--- this will NOT work
Select Id from Contact Where Name = 'William Jones'
--- this will work
Select Id from Contact Where FirstName = 'William’ And LastName ='Jones'
Filter Records by Strings
You can search for records using strings. However, commas in strings act as OR statements. If your string includes a comma, use quotation marks around the string. For example, a search for Universal Containers, Inc, Berlin returns records that include the full string including the comma. Searches for Universal Containers, Inc, Berlin returns records that include Universal Containers or Inc or Berlin.
SOQL GROUP BY Statements
You can use most of the SOQL statements with deterministic encryption. One exception is GROUP BY, which isn’t supported, even though you can group report results by row or column.
SOQL LIKE and STARTS WITH Statements
Deterministic encryption only supports exact, case-sensitive matches. Comparison operators that return partial matches aren’t supported. For example, LIKE and STARTS WITH statements aren’t supported.
SOQL ORDER BY Statements
Because deterministic encryption doesn’t maintain the sort order of encrypted data in the database, ORDER BY isn’t supported.
Indexes
Deterministic encryption supports single-column indexes, single-column case-sensitive unique indexes, two-column indexes, and custom indexes on standard and custom fields.