Salesforce Shield
Shield Product Demo
Tighten Your Security with Salesforce Shield Platform Encryption
What is encryption?
Encryption is the process of encoding a message or information (plaintext) in such a way that only authorized parties can access it.

In an encryption scheme, the intended information or message, referred to as plaintext, is encrypted using an encryption algorithm ( a cipher ) for generating ciphertext that can be read only if decrypted.
In [1]: from cryptography.fernet import Fernet
In [2]: key = Fernet.generate_key()
In [3]: print (key)
b'TiXtMKXGFtUAGV7i4jhmmocouDTbWNP58Esmc3WjVSM='
In [4]: cipher_suite = Fernet(key)
In [5]: cipher_text = cipher_suite.encrypt(b"A really secret message. Not for prying eyes.")
In [6]: print(cipher_text)
b'gAAAAABbuic-j1EGQw45JiZRTHnbbMV2-Ky4MiXxbxTxZal4PQL4XyaXVNn1Z9QkThAHUXV9QfwIZJB7t-a4K-zXVZaxY7KuSQjmD0DqYaZZgs5qoGyB
nU85Zy7JN-f_GzyZdTqVZWiB'
In [7]: plain_text = cipher_suite.decrypt(cipher_text)
In [8]: print (plain_text)
b'A really secret message. Not for prying eyes.'
An encryption scheme usually uses a pseudo-random encryption key generated by an algorithm.
Salesforce platform features & need for Shield Platform Encryption
Field-Level-Security (FLS)
FLS allows you control over who can access and edit certain fields on specific records.
Authentication and Authorization
Authentication and authorization techniques also allow you to control not only who sees what data, but at what time, and from which locations and devices.
Monitor Activities
With tools like the Security Health Check and Event Monitoring.
Need for extra encrypting data to meet industry and regulatory requirements
- keeping customer data secure
- contractual obligations and internal compliance policies emphasize protecting client and customer data
- need for encryption as another access control tool for securing data at rest
So, Shield Platform Encryption can be an this effective additional layer of compliance. Your security, legal, and regulatory specialist can take your organization through a formal security evaluation and help you find the best solution.
Shield Platform Encryption
Shield Platform Encryption should only be implemented after careful consideration:
- an analysis of the kinds of threats your organization should protect against
- which Salesforce security controls can best help you protect against those threats.
Shield : Advanced key derivation system
Key
String of bits that is used for scrambling and unscrambling the data.
Single key - data can be scrambled and unscrambled using a single key
Key-pair - data is scrambled using one key and unscrambled using another key
Key Chain
Keys
Keys for keys: (required before you can use the key)
Master Secrets Salesforce generates new master-secret 3 times year with each release.
A dedicated processor - Hardware-Security-Module (HSM) specially designed for creating strong & secure cryptographic keys.
HSM is on a USB stick - is stored in bank-safety-deposit-box
During each release, designated Salesforce security officers can access the HSM stored in this safety deposit box
They then use the HSM to generate a new master secret, which is stored in a secure area of our servers.
Tenant Secrets
- You create your own tenant secret on demand in Salesforce, we store it securely in the database. You can update your tenant secrets as often as you want.
Your tenant secret partners with the master secret in what’s called a key derivation process to create keys that encrypt and decrypt your data.
Classic Encryption
- Create a custom-text-field to store the data you want to encrypt. The data is encrypted using 128-bit AES (Advanced Encryption Standard) keys

Shield Platform Encryption
You can encrypt all kinds of confidential and sensitive data at rest on the Salesforce Platform using 256-bit AES key.
Subscribers can manage access to their data with a wider range of keys and permissions. Shield Platform Encryption even allows you to search for encrypted data in databases.
To enable Shield Platform Encryption, you need the Customize Application and Manage Encryption Keys permission
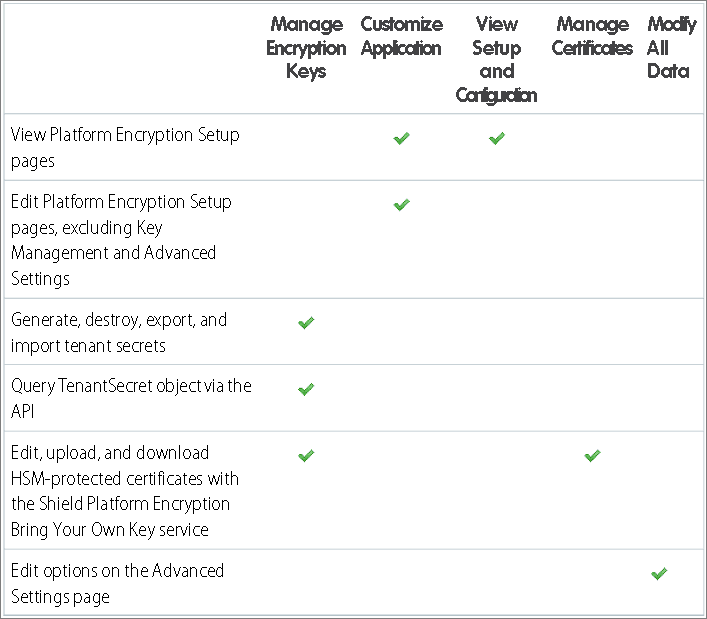
As an admin, assign yourself the View Setup and Configuration permission. This lets you enable encryption features for fields, files, attachments, and apps.
When you have your license and permissions set up, you can enable Shield Platform Encryption on your orgs. You can then create org-specific tenant secrets and customize your encryption settings for each org.
Shield Platform Encryption Setup demo
